Packer – How packer has simplified Cloud provisioning
What is Packer –
Packer (HashiCorp) is an open source tool for creating identical machine images for multiple platforms from a single source configuration. Packer is lightweight, creating machine images for multiple platforms in parallel. Packer does not replace configuration management like Chef or Puppet. In fact, when building images, Packer can use tools like Chef or Puppet to install software onto the image.
A machine image is a single static unit that contains a per-configured operating system and installed software which is used to quickly create new running machines. Machine image formats change for each platform. Some examples include AMIs for EC2, VMDK/VMX files for VMware, OVF exports for VirtualBox, etc.
Packer and Continuous Delivery (CD) –
Packer is lightweight, portable, and command-line driven. This makes it the perfect tool to put in the middle of your continuous delivery pipeline. As part of this pipeline, the newly created images can then be launched and tested, verifying the infrastructure changes work. If the tests pass, you can be confident that the image will work when deployed. This brings a new level of stability and testability to infrastructure changes.

Packer template –
A Packer template is a configuration file that defines the image you want to build and how to build it. Packer templates use the Hashicorp Configuration Language (HCL). Packer configuration has different block in configuration like mentioned below…
- Packer Block – The
packer {}block contains Packer settings, including specifying a required Packer version.
- Source Block – The
source {}block configures a specific builder plugin, which is then invoked by abuildblock. Source blocks use builders and communicators to define what kind of virtualization to use, how to launch the image you want to provision, and how to connect to it.
- Build block – The
build{ } block defines what Packer should do with the Virtual Machine or Docker container after it launches.
Builders are responsible for creating machines and generating images from them for various platforms. For example, there are separate builders for EC2, VMware, VirtualBox, etc.
Please find the supported builder list here – https://www.packer.io/docs/builders
- virtualbox-iso
-vmware-iso
- hyperv-iso
- docker
- Provisioner block – The
provisioner{ } block defines what Packer should do with the image build or Docker container after it launches.
Provisioners use builtin and third-party software to install and configure the machine image after booting. Provisioners prepare the system for use, so common use cases for provisioners include:
- installing packages
- patching the kernel
- creating users
- downloading application code
- Post-Processors – Post-processors run after the image is built by the builder and provisioned by the provisioner(s). Post-processors are optional, and they can be used to upload artifacts, re-package, or more.
- Communicators – are the mechanism Packer uses to upload files, execute scripts, etc. with the machine being created.
Communicators are configured within the builder section. Packer currently supports three kinds of communicators:
none– No communicator will be used. If this is set, most provisioners also can’t be used.- ssh – An SSH connection will be established to the machine. This is usually the default.
- winrm – A WinRM connection will be established.
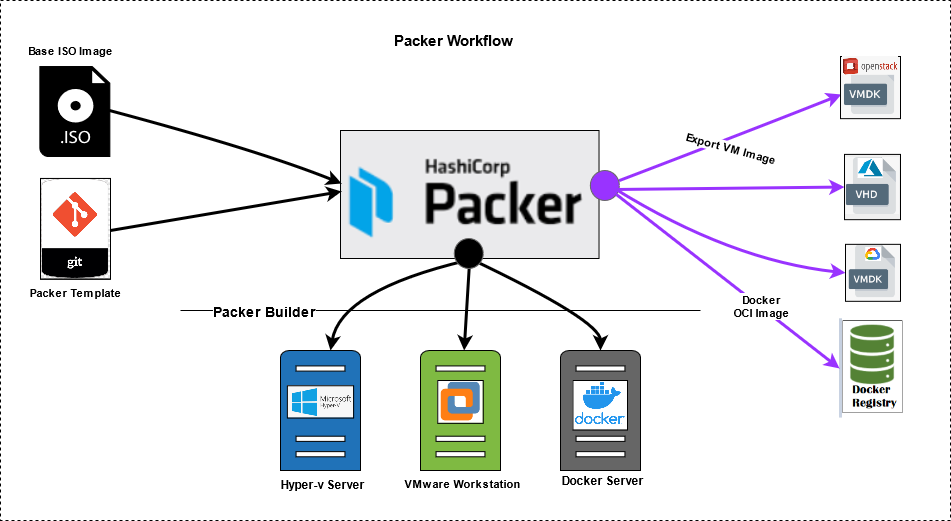
Packer Workflow –
The Packer workflow takes a defined source (usually an operating system installation media in ISO format or an existing machine), creates a machine on the builder, executes the Provisioner’s defined tasks and generates an output. Doing this on Hyper-V, VMWare workstation and Docker may look like what is shown below.
How to use Packer –
Initialize your Packer configuration and check and validate packer template…
$ packer init .
$ packer fmt .
$ packer validate .
Build the image with the packer build command. Packer will print output like what is shown below.
$ packer build new-os-image-template.hcl
Reference –
Packer software – https://www.packer.io
Thank you,
Arun Bagul
(Personal Blog and This is based on my knowledge)


